gustavorwm
Chevereto Member
I don't know much about this, but my VPS stopped working, I contacted my VPS administrator and he told me that the DATA CENTER told him that there was Pishing on my Chevereto installation.
Datacenter:
Below is the list of URLs that point to the phishing web page you are hosting:
* hxxpx: / / tibiagallery [.] com / images / 2020 / [.] progress / index [.] php? email =
▶ Reproduction steps
All the sites that are hosted on the Vps stopped working.
📃 Error log message
LOG ATTACH
📃 Temporary solution
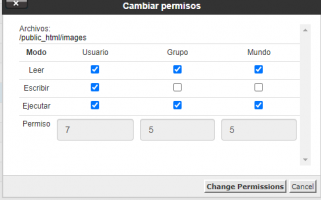
My system administrator reported that a virus entered 7 hours ago, and I add these lines to the htaccess file to stop it.
<FilesMatch "^ \.">
Order allow, deny
Deny from all
</FilesMatch>
Sorry for my bad English.
Datacenter:
Below is the list of URLs that point to the phishing web page you are hosting:
* hxxpx: / / tibiagallery [.] com / images / 2020 / [.] progress / index [.] php? email =
▶ Reproduction steps
All the sites that are hosted on the Vps stopped working.
📃 Error log message
LOG ATTACH
📃 Temporary solution
My system administrator reported that a virus entered 7 hours ago, and I add these lines to the htaccess file to stop it.
<FilesMatch "^ \.">
Order allow, deny
Deny from all
</FilesMatch>
Sorry for my bad English.