Seongil Wi
Chevereto Noob
Hi,
Our research team in KAIST WSP Lab found a reflected vulnerability in chevereto-free (https://github.com/Chevereto/Chevereto-Free).
I post this thread to report the found bug
- Description: An reflected XSS vulnerability was identified in the
▶ Reproduction steps
Reflected Cross-Site Scripting (XSS) may allow an attacker to execute JavaScript code in the context of the victim’s browser. This may lead to unauthorized actions being performed, unauthorized access to data, stealing of session information, denial of service, etc. An attacker needs to coerce a user into visiting a link with the XSS payload to be properly exploited against a victim.
📃 Error log message
Our research team in KAIST WSP Lab found a reflected vulnerability in chevereto-free (https://github.com/Chevereto/Chevereto-Free).
I post this thread to report the found bug
- Description: An reflected XSS vulnerability was identified in the
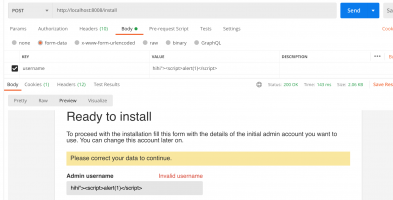
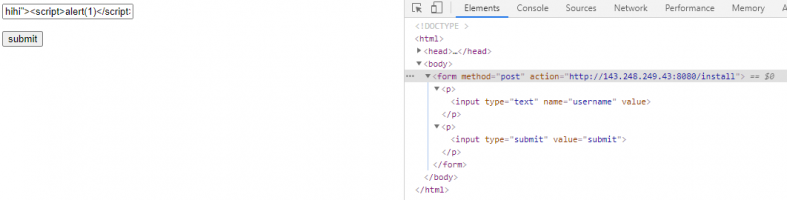
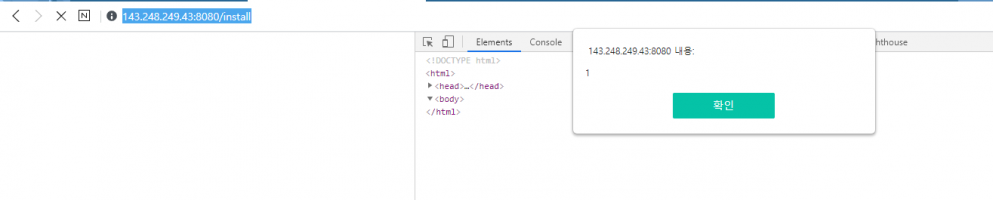
ready.php page in the installation process due to insufficient sanitization of the $_POST['username'] variable. As a result, arbitrary Javascript code can get executed.▶ Reproduction steps
- Install the Chevereto until the ready status (after connection with DB. Note that when we install the app with Docker compose, we can go to the ready state directly)
- Access to the
http://[localhost]/installusing post request withusernameparameter. The value of the parameter should behihi"><script>alert(1)</script>
Reflected Cross-Site Scripting (XSS) may allow an attacker to execute JavaScript code in the context of the victim’s browser. This may lead to unauthorized actions being performed, unauthorized access to data, stealing of session information, denial of service, etc. An attacker needs to coerce a user into visiting a link with the XSS payload to be properly exploited against a victim.
📃 Error log message